Server Backup Manager creates backups using the Virtual Full Backup method. First, SBM creates the initial full backup, or initial replica. After that, each time a replication executes, SBM stores only the differences (or block-level deltas) that have occurred since the last replication. The following image illustrates the size of data for each replication.
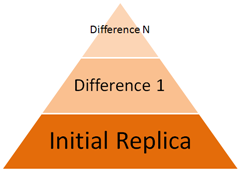
Each replication creates a point-in-time image of the device. This image is called a recovery point. Server Backup Manager uses the block deltas database to map the block versions and recovery points. This database is called a Disk Safe. The following image illustrates the information within a Disk Safe.
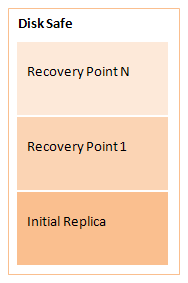
SBM uses a Disk Safe to keep and arrange the pieces of replicated information. A Disk Safe can be defined as a container for the data necessary for a restore. You can restore from any available recovery point in any Disk Safe.
Disk Safes have one or more assigned devices selected for backup. Note that you can assign one device to multiple Disk Safes.
| Notice You cannot begin backing up a device until a Disk Safe is created to act as the back up repository. |
To run a replication, you need to associate a data protection policy with your Disk Safe. The policy backs up devices associated with the Disk Safe. If there are items you do not want to include in the replication, you can exclude selected files and folders from the replication when defining the policy properties.
On a physical level, a Disk Safe is a directory containing the following files and folders:
- .db file
- .db-journal file
- .ebs file
- metadata folder
Properties of a Disk Safe
Disk Safes have the following properties, which you define when creating the Disk Safe:
- Identification. A unique name that distinguishes this specific Disk Safe in a list and while defining policies.
- Disk Safe Location. The physical location where the Disk Safe is saved.
- Devices. A list of devices associated with this Disk Safe. Server Backup Manager automatically identifies and adds all devices during Disk Safe creation. You can also manually add one or more hard disks, partitions, and other volumes of a server where file systems are mounted as devices.
- Compression Type. Type of data compression used on this Disk Safe. Compressing data helps reduce the consumption of hard disk space or transmission bandwidth.
- Encryption. Type of data encryption used on this Disk Safe. Encryption helps to protect your Disk Safe data from unauthorized access. When using encryption, your data is converted to cipher text.
Use the Server Backup Manager Web interface to change these characteristics for an existing Disk Safe, with the exception of Disk Safe Location, Encryption, and Deduplication.
The following additional properties are available for existing Disk Safes:
- State
- Recovery Points
- Archive Points
- On Disk Size
States of a Disk Safe
Disk Safes exist in one of the following states:
- Opened. An Opened Disk Safe allows you to associate tasks including Backup with opened Disk Safes, and browse the recovery points of a task.
- Closed. A Closed Disk Safe prevents any tasks associated with it from running. You also cannot browse the recovery points contained within the Disk Safe.
Available Disk Safe tasks
The following actions are available with any Disk Safe:
- Create a new Disk Safe
- Edit an existing Disk Safe
- Attach (open) an existing Disk Safe in the system
- Close (disable) a Disk Safe
- Detach a Disk Safe
- Delete a Disk Safe and all its data
- Vacuum a Disk Safe
- Browse recovery points contained within Disk Safes
- Move a Disk Safe from one location to another
- Copy a Disk Safe from one Backup Manager to another
- Copy a Disk Safe across Windows/Linux platforms

Tip
You can move a Disk Safe using a tool like Windows Explorer drag-and-drop, scp, xcopy, ftp, etc.
- Customize the Disk Safes list — Instructions on how to hide and show columns, sort rows, manage items per page, and filter the Disk Safes list in Server Backup Manager.
- Close Disk Safes — Instructions on how to close or disable Disk Safes in Server Backup Manager.
- Vacuum Disk Safes — Instructions on how to vacuum a Disk Safe in Server Backup Manager.
- Use Disk Safe best practices — Best practices concerning the reliability of Disk Safes and what can corrupt Disk Safes in Server Backup Manager.
- Attach Disk Safes — Instructions on how to attach Disk Safes in Server Backup Manager.
- Detach Disk Safes — Instructions on how to detach Disk Safe configuration but leave all backed up data on disk in Server Backup Manager.
- Delete Disk Safes — Instructions on how to delete Disk Safes and their data in Server Backup Manager.
- Copy or move Disk Safes — Instructions on how to copy or move Disk Safes to another place on the same Backup Manager or to another Backup Manager.
- Store Disk Safes on a Windows network share — Instructions on how to save Disk Safes on a Windows Network Share using Server Backup Manager.
- Access Disk Safes — Instructions on how to access and use the Disk Safes window in Server Backup Manager.
- Create Disk Safes — Instructions on how to create a new Disk Safe in Server Backup Manager.
- Edit Disk Safes — Instructions on how to change the properties of existing Disk Safes in Server Backup Manager.
- Manage Disk Safe encryption — Instructions on how to manage Disk Safe encryption in Server Backup Manager.
- Schedule Disk Safe verification — Instructions on how to schedule Disk Safe verification in Server Backup Manager.
- Run Disk Safe verification — Instructions on how to run a Disk Safe verification manually in Server Backup Manager.
- Use Disk Safe Replication — Instructions on how to create a replica Disk Safe in Server Backup Manager.
- What Is Docstore?
